


Physical Security
Looking at a typical SCADA configuration (see figure below), it’s plain to see that physical security is a challenging task when your resources are located in several locations… sometimes hundreds of miles apart!
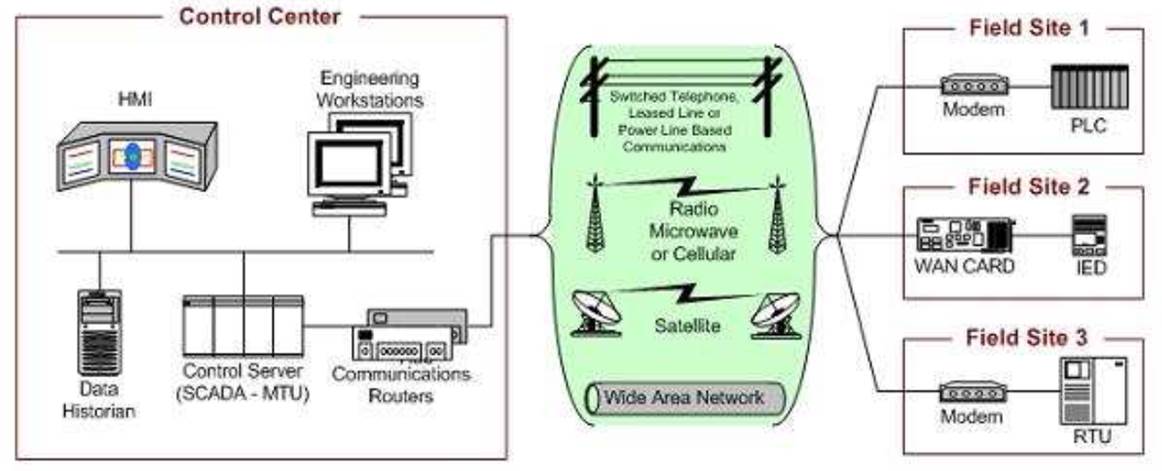
Typical Structure of a SCADA system
Physical security is more than just posting a guard at the front entrance. Tell that to the nuclear power plants that were recently overrun by Russian troops in the Ukraine. The plants are now offline. Millions without power.
A strong physical security strategy has layers of protection to defend against intrusion, surveillance, robbery, terrorism, or just plain vandalism.
Think you know all about physical security? Look at the picture below and name at least 3 things wrong with this doors cypher-lock:

1) Everybody uses the same entrance code (3-4-5-6)
2) Code has never been changed
3) Code is too short/weak/simple
4) Assume that “tail-gating” is also alllowed
5) How many personnel know this code that shouldn’t, including ex/dis-gruntled employees?
A recent intrusion at a hospital saw a PenTester “tail-gate” an employee into the hospital. Once inside, he made his way to the central computer data center where he plugged an RF-USB device into the back of a computer (undetected), retreated to his hotel room nearby, and was able to steal ALL the hospitals patient medical records! BTW… Medical records can fetch more than $1000 per record on the black market. Even nation-states are very interested in medical records, credit card info, etc.
Intrusion Countermeasures should be implemented wherever your assets are located.
Physical Security – Protect your companies private property, buildings, and physical assets from intrusion, destruction, and occupation.
Disaster recovery/business continuity planning - Tools and procedures for responding to unplanned events, such as natural disasters, power outages, intrusion, or cybersecurity incidents, with minimal disruption to key operations.
We can provide all of this protection, and more!
“Quality Work… for a Quality Wage”
© 2026 Houdini Security Global – All Rights Reserved