


Cyber Theater
First, you probably need a couple of definitions for those non-technical people:
Obscurity - ŏb-skyoo͝r′ĭ-tē, əb- noun –
1. Deficiency or absence of light; darkness.
2. The quality or condition of being unknown.
3. One that is unknown.
SCADA - Supervisory Control And Data Acquisition (SCADA) is a control system architecture comprising computers, networked data communications and graphical user interfaces for high-level supervision of machines and processes.
ICS – An Industrial Control System (ICS) is an electronic control system and associated instrumentation used for industrial process control. Control systems can range in size from a few modular panel-mounted controllers to large interconnected and interactive distributed control systems (DCSs) with many thousands of field connections.
PLC – Programmable Logic Controller - A programmable logic controller or programmable controller is an industrial computer that has been ruggedized and adapted for the control of manufacturing processes, such as assembly lines, machines, robotic devices, or any activity that requires high reliability, ease of programming, and process fault diagnosis.
IoT – the Internet of Things describes devices with sensors, processing ability, software and other technologies that connect and exchange data with other devices and systems over the Internet or other communications networks.
And finally,
Cyber Theater (security thru obscurity)
“Security Theater is the practice of taking security measures that are considered to provide the feeling of improved security while doing little or nothing to achieve it.” “Cyber Theater is nothing more than Security Theater wrapped in additional obscurity! “Several business entities come to mind immediately when Cyber Theater is mentioned… SCADA/ICS systems, IoT, network communications, and satellite security. Breaking down these security myths by entity, might shed some light on how you should look at and be very aware of what’s fact and what’s fiction.
SCADA/ICS - In the good ol’ days, maintenance workers drove specially equipped trucks from one water tank/water tower to another (usually “hidden” away on a hill, unnoticed) to take measurements and readings from the sensors there, such as water temperatures, water levels, water pressure in the pumping system, etc., to make daily observations and readings. These workers were replaced by automated sensors, small computers, and radio transmitters that reported in real-time back to a central office where a console operator monitors those readings by sitting in front of a computer and looking at a big monitor that visually shows the data in a schematic-like diagram on a computer screen (see pictures below). The system sounds an alarm (audibly or visually) when readings aren’t within the specifications set forth by the water district (i.e. high/low pressure, over-under temp, high/low water level, etc.)


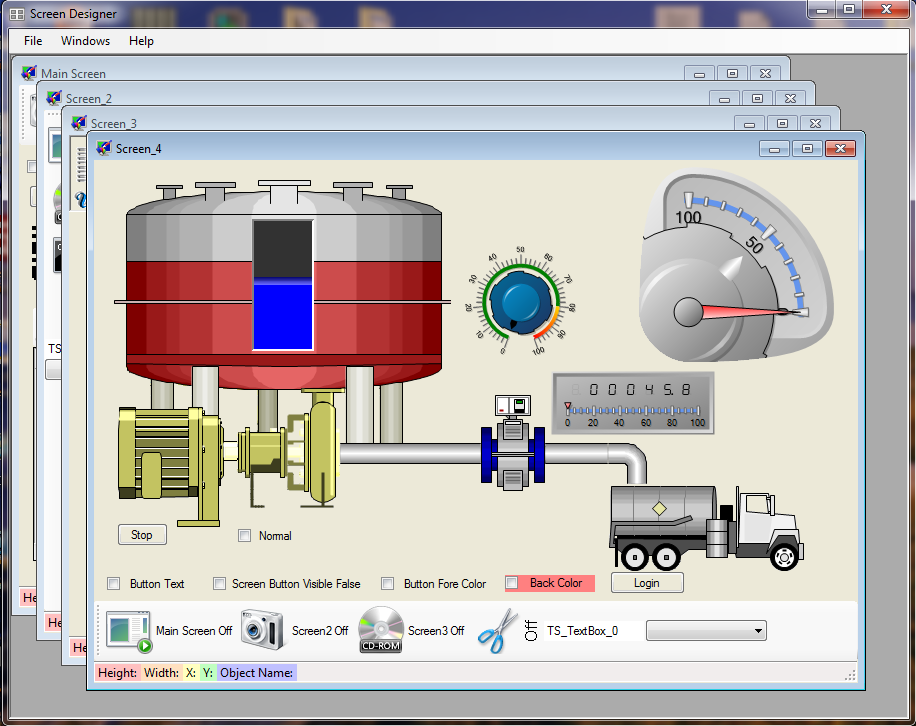

Today, modern SCADA systems rely on radio transmissions to send pertinent data from the remote site, back to the main office where the SCADA operator monitors all the devices on his HMI (Human-Machine Interface) screens. BTW… these radios are Commercial Of The Shelf (COTS) radios that can be purchased by you and me. Because some SCADA devices (sensors, PLC’s, etc.) date back 40 years or more, think back to that time. Cyber security didn’t even have a name yet, so built-in security didn’t existent or was lame to say the least! Don’t let anyone tell you that security is at it’s best in the SCADA/ICS world, and that you have nothing to worry about (“pay no attention to that man behind the curtain’)… How can it be true when some of these places are still using 40+ year old equipment? Besides (tongue-in-cheek), who would ever want to tamper with your drinking water, electricity, or other infra-structure items we take for granted? And who knows anything about the programs that control these devices (called ladder logic, another antique programming language used to program those PLC’s?). “We’re safe, I tell you!” An example of SECURITY THROUGH OBSCURITY!
Network and satellite communications – How much do you know about satellite communications, or even your own wireless router? Well, back in the late 1950’s and early 1960’s no one ever thought that hackers would ever infiltrate our satellites… I mean after all they were owned by the government, very expensive, one-of-a-kind, and they’re 100-1,000 miles up in space! And (again) “trust us, they’re secure!” was the battle cry. That’s why recently (July 2023), 3 researchers from the Netherlands broke the almost elementary but still proprietary security algorithms that encompass a lot of satellites. The protocol was hacked within 1 minute using today’s fast, smart (AI), and robust computers. And all this time the geniuses at space agencies and private enterprises never thought about security for those orbiting targets because after all, they’re so far away and traveling so fast… They dazzled us with their techno-talk and space jargon, distracting us like a little boy with ADHD given a shiny new fidget spinner! Yet another example of SECURITY THROUGH OBSCURITY!
Our point about all this is simple… SECURITY THROUGH OBSCURITY is not a viable excuse to use on the public to put their minds at ease about security. It’s unacceptable. Artificial Intelligence, computing power, network speeds, and sophisticated hackers are using tools, techniques, and tricks* we couldn’t even envision just 12 months ago! It’s possible (and proven) that hackers can break into your phone or computer through your toaster oven or other IoT devices! How about hacking your mobile phone while it’s turned off! Fake news and misinformation is one thing. SECURITY THROUGH OBSCURITY is another.
*BTW… Who’s using these tools, techniques, and tricks to infiltrate/invade our infrastructure?
你会说中文吗?
(Translation: Can you speak Chinese?). And there are other nation states hacking their way into your life and our infrastructure. HINT: They’re already here, inside our devices, patiently waiting for the right time to spring into action and wreak havoc. It’s time to expect security transparency and accountability, regardless of the fake news, misinformation, myths, rumors. lies, deceit, and in general “pull the wool over their eyes and inundate them with techno-speak, buzzwords & B.S.” Security needs to be more than lip service and taken very seriously. Contact us… We can help.
“Quality Work… for a Quality Wage”
© 2026 Houdini Security Global – All Rights Reserved