


SCADA Protection
Supervisory control and data acquisition (SCADA) is a control system architecture comprising computers, networked data communications and graphical user interfaces for high-level supervision of machines and processes. It also covers sensors and other devices, such as programmable logic controllers, which interface with process plant or machinery.
SCADA Security is a broad term used to describe the protection of SCADA networks. These networks are made up of computer hardware and applications and are utilized to control and monitor vital infrastructure in nations where they are employed. Some of the systems utilizing SCADA networks include natural gas, electricity, water, and other key services.
Due to the valuable role and vulnerabilities of these networks, measures are taken by governments and private companies to ensure the safety of these systems. SCADA security is a term to describe measures taken to protect SCADA networks as well as to discuss vulnerabilities (i.e. common SCADA security problems).
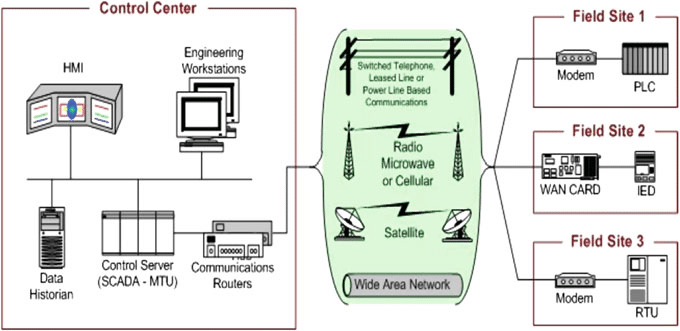
General Structure of a SCADA system
A strong cybersecurity strategy has layers of protection to defend against cyber crime, including cyber attacks that attempt to access, change, or destroy data; extort money from users or the organization; or aim to disrupt normal business operations. Countermeasures should address:
Critical infrastructure security - Practices for protecting the computer systems, networks, and other assets that society relies upon for national security, economic health, and/or public safety. The National Institute of Standards and Technology (NIST) has created a cybersecurity framework to help organizations in this area, while the U.S. Department of Homeland Security (DHS) provides additional guidance.
Physical Security – Protect your companies private property, buildings, and physical assets from intrusion, destruction, and occupation.
Network security - Security measures for protecting a computer network from intruders, including both wired and wireless (Wi-Fi) connections.
Application security - Processes that help protect applications operating on-premises and in the cloud. Security should be built into applications at the design stage, with considerations for how data is handled, user authentication, etc.
Cloud security - Specifically, true confidential computing that encrypts cloud data at rest (in storage), in motion (as it travels to, from and within the cloud) and in use (during processing) to support customer privacy, business requirements and regulatory compliance standards.
Information security - Data protection measures, such as the General Data Protection Regulation or GDPR, that secure your most sensitive data from unauthorized access, exposure, or theft.
End-user, Customer, and Vendor education - Building security awareness across the organization to strengthen endpoint security. For example, users can be trained to delete suspicious email attachments, avoid using unknown USB devices, etc.
Disaster recovery/business continuity planning - Tools and procedures for responding to unplanned events, such as natural disasters, power outages, or cybersecurity incidents, with minimal disruption to key operations.
Storage security - Solid data resilience should contain numerous safeguards. This includes encryption and immutable and isolated data copies. They should remain in the same pool so they can quickly be restored to support recovery, minimizing the impact of a cyber attack.
Mobile security - Enables you to manage and secure your mobile workforce with app security, container app security and secure communications.
We can provide all of this protection, and more!
“Quality Work… for a Quality Wage”
2025 Houdini Security Global – All Rights Reserved